Frankfurt DE-FRA-1
The German DE-FRA-1 datacenter is ideally placed to serve teams looking for GDPR-compliant cloud servers. Hosted by the Equinix data center facility.
We are multihomed on all locations; connected directly to different Tier 1 and Tier 2 transit providers with multiple 10 Gbps links. Several peering connections with major local actors grant first in class performance in our geographical area. Internal networking is supported by a robust 100 Gbps backbone.
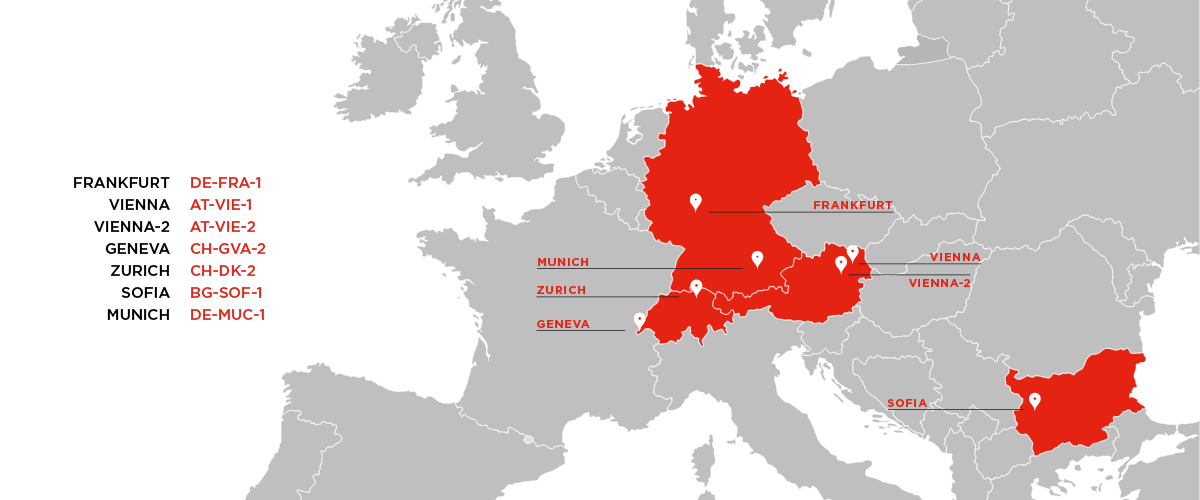
The German DE-FRA-1 datacenter is ideally placed to serve teams looking for GDPR-compliant cloud servers. Hosted by the Equinix data center facility.
With the Munich zone, industries and financial ecosystem of the region can get access low latency cloud hosting and leverage DE-MUC-1 either as a primary or secondary site for business critical applications.
Located in the Arsenal, a former military complex, our location in Vienna follows our strict requirements for data center choices.
Located in the A1 Next Generation Data Center, a state-of-the-art data center, our second location in Vienna is one of our most modern data center facilities.
Placed close to European financial ecosystems and global markets, CH-GV-2 is hosted by the Equinix data center facility.
Based in one of the latest Equinix datacenters in Switzerland, CH-DK-2 is placed in the middle of Switzerland's densest network exchange point.
Our Zone in Sofia aims to empower the thriving startups, SMBs and Enterprise businesses in Southeastern Europe with the IaaS resources they need.





Start moving your workloads to the cloud to keep them under strict GDPR compliance and close to your business.